Basic Hygiene
1. Know your data and where it is stored – maintain an up-to-date inventory (e.g., laptops, PCs, servers, software, media (USB, CD-ROM, DVD), hosted cloud storage).
2. Back up data regularly and test periodically – online and offline. Backups need to be physically separate (on a different system) from the primary copy of data. There are services available on campus to assist with this.
3. Use strong passwords of at least 12 characters or more and multi-factor authentication (e.g., DUO).
4. Ensure anti-malware software is installed, running and up to date. Your local IT unit can assist in getting this in place.
5. Apply patches regularly and use supported operating systems and applications.
6. Vet security practices of 3rd parties (e.g., SaaS Software-as-a-Service providers) before placing valuable research data in these environments and ensure compliance.
7. Delete inactive accounts.
8. Use encrypted secure remote access services such as virtual private network (i.e., VPN) when accessing systems remotely.
9. Remain vigilant in avoiding phishing and social engineering attacks.
10. Determine if additional protective measures are required for your specific research program ( E.g., Basic Safeguarding, dbGAP, IRB and others)
11. Classify your research data into one of the four standard protection levels (P1,P2,P3,P4). Your UISL is a helpful local resource to assist you in this.
12. Consider housing your data in a managed on premise or enterprise-approved cloud environment, e.g., UCI’s Secure Research Environment (SRE) or Campus Research Storage Pool (CRSP), Microsoft OneDrive. These are existing services on campus and available to you. Please refer to the chart below for additional details.
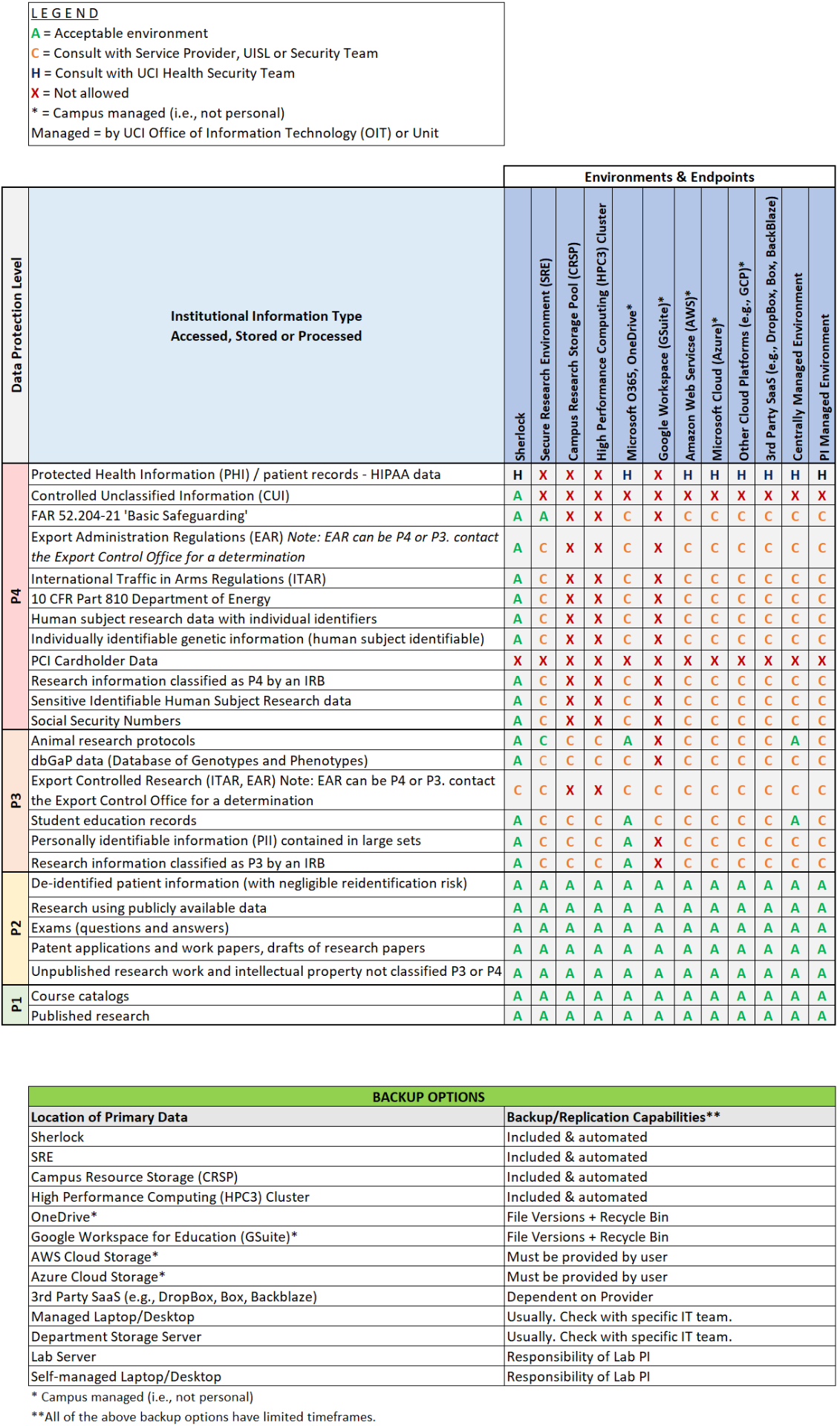
Research | Environment Mapping
Selecting the appropriate environments and endpoints for your research is critical. The table below maps data to acceptable environments and endpoints by protection level. Note that selection and use of an acceptable environment does not automatically guarantee compliance. Researchers must maintain awareness of and comply with security requirements of the applicable framework(s).